Workday goes live at the Universities of Wisconsin on July 7, 2025. As we begin to use Workday, we must keep in mind that cybercriminals often target organizations that are changing systems. Other universities have seen an increase in phishing emails and scam calls with similar large-scale implementations. You can help keep the UWs’ information secure by watching for and reporting phishing attempts.
Recognize Phishing Red Flags
- Someone pretending to be a colleague: Scammers might send emails or call pretending to be someone you know. They might ask you to change settings for something like where a paycheck goes.
- Fake vendor messages: You may get a message from someone claiming to be from a company we work with asking to update banking information.
- Password phishing: You may get an email asking that you share your login information.
- Bogus Workday notifications: You may see fake emails that look like they’re from Workday, with links you shouldn’t click. The presence of an official logo does not guarantee the authenticity of an email.
- Rush tactics: Beware of messages claiming you need to act right away about your paycheck or account, trying to make you hurry and not think things through.
Examples of Workday Phishing Emails
Erroneous Login Page
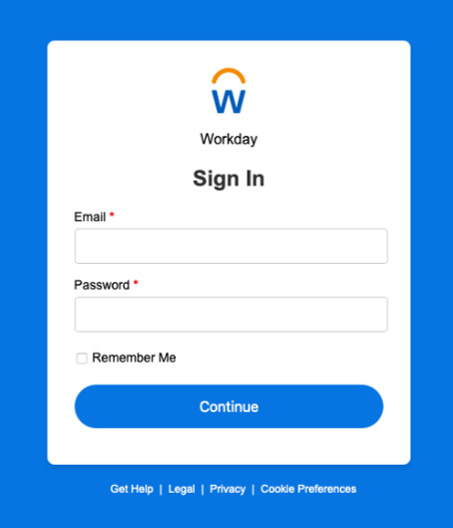
Phony Service Offerings in Workday
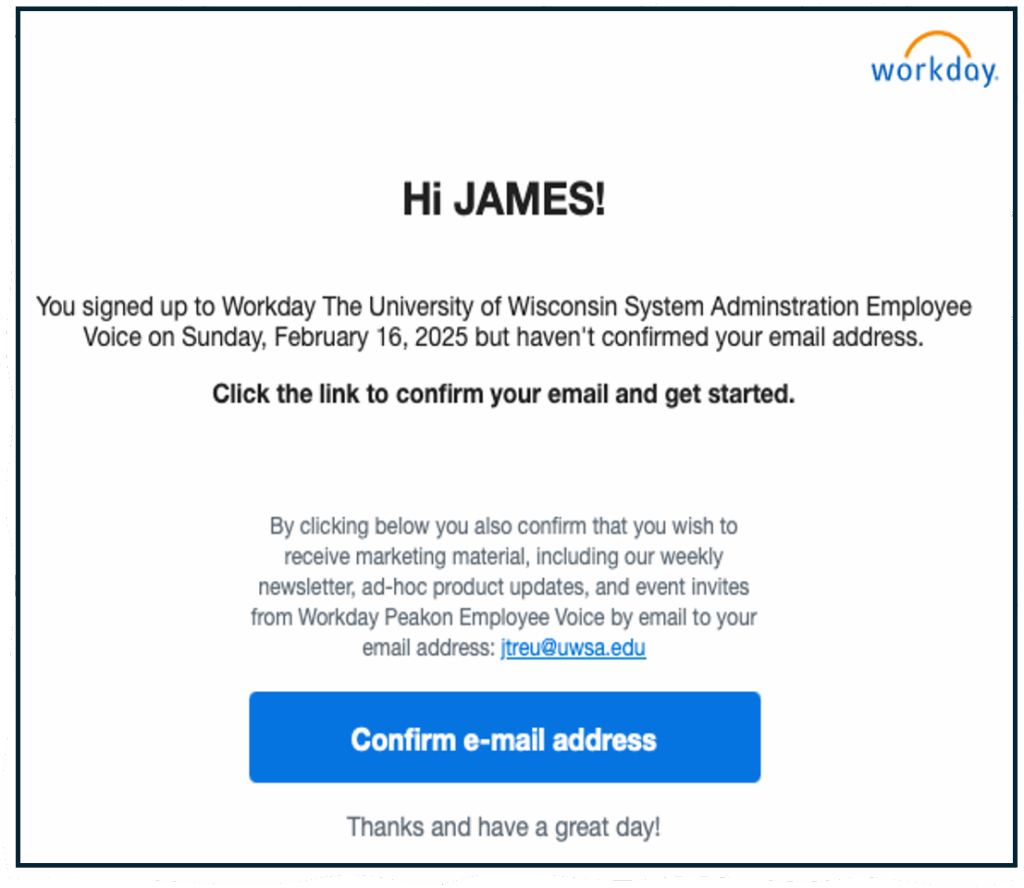
Fake Offers of Assistance
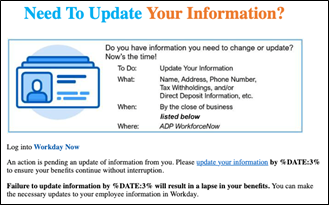
How to Spot Real Workday Messages
Legitimate Workday communications will come from known sources and usually through multiple channels:
- Announcements within the Workday system itself
- Official university newsletters or emails
How to Stay Secure During the Transition
- Check who’s sending: Look for subtle variations from legitimate UW email domains and addresses.
- Emails sent directly from the Workday system will be from wisconsin@myworkday.com
- All other UW emails related to Workday or from our support teams will end in wisconsin.edu (UW Administration) or wisc.edu (UW–Madison). These addresses will also include a preceding reference to the support function such as: @uwss.wisconsin.edu; @support.wisconsin.edu; @vc.wisc.edu. To the left of the @, you will see serviceoperations, servicedesk, enterprisedesk, or RAMP.
- Be careful with links: Take a good look at Workday-related emails before clicking links or attachments. Before you click, ask yourself, “Does this seem legitimate?” and always be intentional before taking any action.
- Use official sources and the right login page: Always log in through the official UW Workday portal instead of following email links. Access Workday by going directly to the Workday icon on your My Apps (Okta) homepage or my.wisc.edu portal for UW–Madison.
- Protect your credentials: Remember that your login credentials are yours alone — never share it, even with coworkers or IT staff. Legitimate support staff will never ask for your password. Never enter your credentials into links from unsolicited emails or messages.
- Use multifactor authentication: Workday will ask for MFA when you log in. If it doesn’t ask after you enter your password, stop and contact your campus IT help desk.
- Watch for random MFA prompts: If you get MFA prompts you didn’t initiate, don’t accept them, and call your campus IT help desk.
- Report “phishy” email: If you get a questionable Workday-related email, report it to your organization’s IT or security team immediately. Do not reply or click on links.
How Workday Protects Our Data
- Data encryption: Workday encrypts all customer data and secures information being sent back and forth.
- Login security: Workday will use multifactor authentication, and people will only be able to see the information they need for their job.
- Secure facilities: Workday’s systems are in secure data centers with multiple security layers, including biometric verification and 24/7 monitoring.
- Ongoing security checks: Workday regularly tests for vulnerabilities and has outside experts conduct security assessments.
- Multifactor authentication: Our Workday implementation features multifactor authentication via Okta and Duo (UW–Madison) to create a barrier to entry for credential phishers who may try to log into your account.
- More information about Workday security features is available on the company’s website.
By using Workday’s security features and following good phishing awareness practices, we can protect the UW’s data during this transition. If something seems off, check with a trusted source. Remember that security is a shared responsibility, and vigilance is key in combating cyber threats.